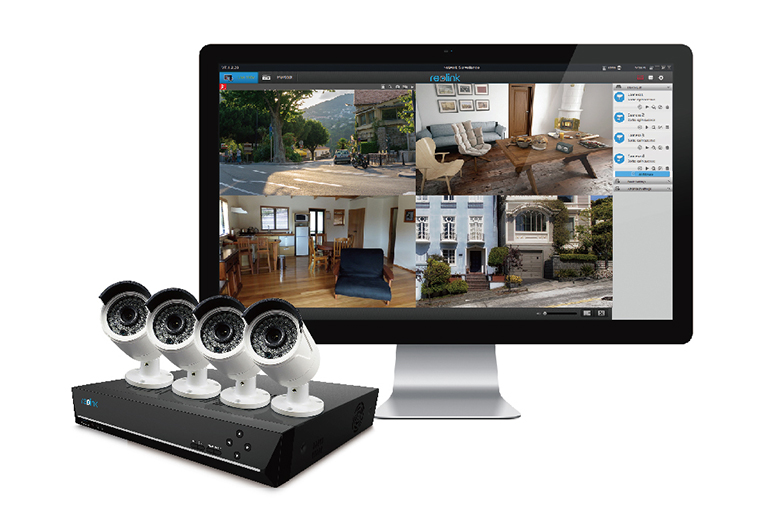
Not known Details About Cctv Installers
Table of ContentsThe Best Strategy To Use For Cctv InstallersThe Only Guide for Security System InstallersThe Main Principles Of Security System Installers Getting The Security Camera Installations Perth To WorkAll about Cctv InstallationsThe smart Trick of Cctv Installers Perth That Nobody is Talking About
Tiny Biz Club is the premier destination for local business proprietors as well as business owners. To do well in organization, you have to regularly learn about new points, assess what you're doing, and also seek ways to improvethat's what we're here to aid you do.Property owners are maintaining up with modern-day times and also updating their homes. Nowadays, residential owners either count on smart technologies that they can integrate into residence automation or mount CCTV cameras. If you wish to participate in on the trend, it is best to begin by setting up security camera systems.

Cctv Installers for Dummies
With this additional feeling of security, you can be certain living your life, recognizing that you and your household are secure. Did you know that having a security system mounted in your house has insurance coverage benefits? If a break-in took place, you could file an insurance claim for burglary or criminal damage.
As a result, the video footage videotaped is solid proof. It is a reward if your recording remains in high-def as you will have a much better sight of the perpetrator's face. Some modern-day security video cameras can even record audio. With these video clips, there is a high opportunity that the authorities can recognize and catch those entailed.
Sometimes, working moms and dads intend to check in with their kids when they return from school. You can quickly do this if your safety and security system includes remote tracking. With this, you can obtain a real-time feed of your home on your smart device or tablet, making it uncomplicated to sign in with the family even when you go to job.
The Best Strategy To Use For Cctv Installers Perth
When you have a safety and security camera system, you can look after them anywhere you may be. Once you have actually installed a protection video camera system on your home, you can use them for years with little maintenance costs.
Not all people at your doorstep rate on your property. In some cases, there are folks you do not intend to unlock for, like a sales rep or a stranger. With a home security system, you do not need to unlock to examine who is behind it.
A residence security system brings an additional layer of defense versus possible burglars. There are multiple choices on the market today in terms of updating the security of your residence. Nowadays, you can have remote tracking features and also video footage with audio. With these innovations, you will certainly be safeguarding on your own, your prized possessions, and also your enjoyed ones.
Cctv Installations Can Be Fun For Everyone

The view of a CCTV electronic camera infers an air of risk and the presence of the law, discouraging any individual planning to accomplish a criminal offense from doing so. CCTV systems are able to track what is occurring at the properties where they are set up. By monitoring the task of employees and site visitors at your company' website, you as well as your labor force can have complete satisfaction concerning specifically what is taking place under your roof covering.
For more details on any of our solutions, or best site for any type of other query, contact us with our friendly team of specialists today as well as we'll be greater than pleased to assist with any kind of inquiries you might have.
Some Of Cctv Installers
Home Information It's not unusual to see CCTV cams located on every corner of every building in business areas. As one of the simplest systems to establish up, and among one of the most economical safety systems, CCTV is used by almost every organization to secure their building, and also nowadays, they're ending up being an extra regular event on homes too, with our team alone installing residential CCTV 4-5 times a week.
Not only is this more secure, it is likewise much less stressful. One more excellent use CCTV is to make use of as a peephole for homes that are without them if you receive a visitor late in the evening as well as are not sure who maybe, you can determine the visitor without having to answer the door.
For even more information, obtain in call (Security System Installers) with our friendly as well as professional team today
The 9-Second Trick For Cctv Installers
Insurer will frequently lower your costs if you have actually CCTV mounted. It's worth calling your insurance company to discover if you can have a price cut on your premium and also conserve cash. These days house CCTV installment is relatively economical. Electronic cameras, electronic video recorders (DVR) and installment by a knowledgeable installer is affordable and also when checking out the advantages above is well worth the price.
There we have 7 essential benefits of CCTV systems, if you do determine visit the website to go ahead as well as have CCTV installed, you might be interested in our article on choosing a CCTV installer.
When it involves CCTV installation, you have two options: tackle it yourself or hire an expert. While there are absolutely advantages to setting up a CCTV system yourselfmostly conserving cash on installationyou'll be these details losing out on some vital benefits that only a pro can offer. Here are seven factors why you ought to hire a pro for CCTV installation.